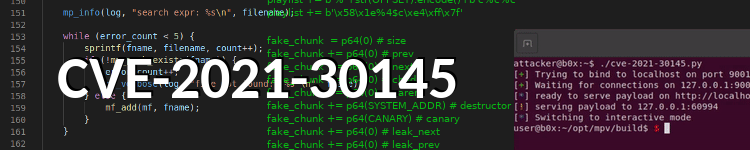
The mpv media player provides a custom protocol handler (mf://) in order to merge multiple images to a video. An undocumented feature within this protocol handler allows the usage of a format specifier in the provided URL, which is evaluated using sprintf. This results in both, a format string vulnerability as well as a heap overflow (CVE-2021-30145).
After disclosing the vulnerability to the mpv team on the 3rd April 2021 I got an immediate response. The mpv team took the issue very seriously and immediately started to work on a patch with me. This was the first time I disclosed a vulnerability to an open source project and I was really impressed about the professional reaction and the passionate commitment. The patch was released only two days after my report on the 5th April 2021 (commit). Thanks a lot to avih, sfan5 and jeeb.
The impact of the format string vulnerability is limited on Linux, because the binary is compiled with FORTIFY_SOURCE by default. Though the heap overflow can be used to gain arbitrary code execution by overflowing into an adjacent heap chunk and setting a function pointer to an attacker controlled value. Nevertheless I estimate the probability of exploitation in real life as quite low, because a victim has to be tricked into opening a malicious playlist (e.g. via a URL like http://10.0.0.1/evil.m3u) and the attacker has to have detailed information about the victim’s system to fine-tune the exploit.
Within this article I describe the vulnerability itself as well as the development of a proof of concept exploit for Ubuntu 20.04.2 LTS with ASLR disabled. At the end of the article I outline a few thoughts on how ASLR can be bypassed and what changes if we develop an exploit for Windows. The article is divided into the following sections:
– Introduction
– Format String Vulnerability
– Heap Overflow
– Exploitation
– Further Thoughts
– Conclusion